How does it work? - How the attackers reach you?
Billing, shipping, invoice related phishing emails. Attackers most frequently use phishing campaigns in which hackers send emails seemingly from a legitimate source requesting passwords or other sensitive information. Criminals have also started using commercial emails containing ransomware to initiate encryption.
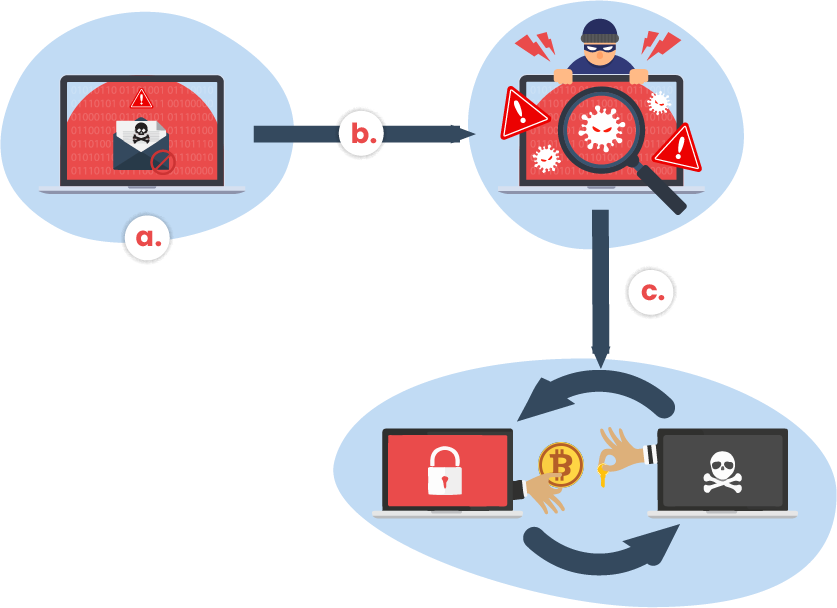
a. Ransomware starts with an unsolicited email, typically designed to trick the victim into clicking on an attachment or visiting a webpage.
b. The ransomware leverages flows in the computer’s operating system to force to run ransomware code.
c. The ransomware encrypts important files on the system and demands a ransom payment using the digital currency bitcoin.
How to minimize the risks?
How to protect your business?
1
Avoid Email Links and Attachments
Phishing attacks are the most common way to spread ransomware. So, avoid opening email attachments or clicking on links, unless you know what it is. Even if you trust the sender be careful because his email account may have been hacked. If you want to find out more info about phishing attacks and how to protect your business, we have a blog post about this.

2
Avoid Pirated software programs
Never install pirated software on your computer and always double-check the software you download. The growing number of ransomware attacks increased lately, due to the ease of downloading software programs. Cybercriminals now host websites from which ransomware programs can be downloaded easily.

3
Keep multiple backups
Back up regularly sensitive and important information. In case of an attack, such a step will allow you to quickly restore all your data and recover from a ransomware attack without paying a ransom to get the data back.
4
Software updates
Constantly, maintain up-to-date security software, operating system, and browsers on your computers.

6
Ad blocker blockers
Use ad blockers to securely navigate on internet. Criminals have also started using compromised advertising (malvertising) to spread ransomware. These can target trusted websites. Ad blockers can protect against malvertising. For example, a good ad blocker is Privacy Badger.

7
Business solutions
For business use, we recommend to centrally manage PCs & Antivirus, enforce security policies and use advanced email protection.

Real-life situation
Your employee is receiving an email from a friend. This includes a link to a fun video. The employee follows the link and clicks on the following pop-ups.
Later that day, his screen starts to change colour, and a window appears informing him that all the files on his computer have been hijacked and encrypted. He will not be able to access anything if he does not pay a ransom. If he chooses not to pay, he may never have access to the files again.
It’s always better to prevent this attack than to try to recover your data after encryption.